Setting up DNSSEC in Porkbun with CloudFlare DNS

Stuck with an obscure DNSSEC configuration error on your Porkbun account? Seeing "We were unable to create the DNSSEC record." with no further pointers was frustrating to me so writing a short note on solving the problem :)

I've had the DNSSEC configuration for this domain on my todo list for almost a month now. Decided to suck it up today and have it crossed out. The reason I've put it away for so long is that the configuration wasn't that straightforward. I ended up with an obscure error when configuring records between DNS server I'm using at CloudFlare and the Porkbun registrar. It is super simple at the end of the day. Just needed to know what not to configure!
Mapping CloudFlare to Porkbun
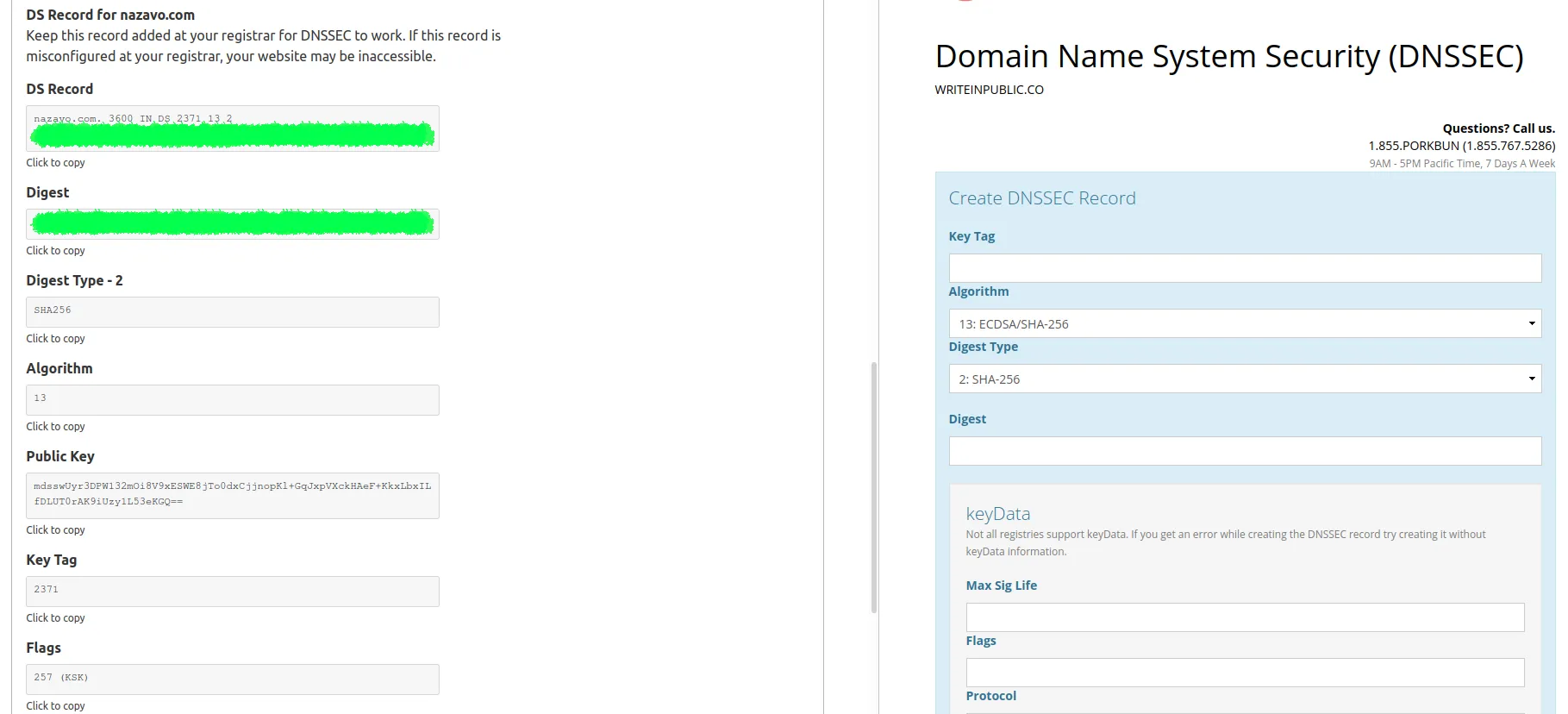
I was stuck for about 20 minutes trying to figure out why Porkbun won't accept the configuration provided by CloudFlare. It all ended up being a simple trick - don't copy all of the values, only the ones needed in the "Create DNSSEC Record" section.
Here's a quick answer: Only fill out the Key Tag, Algorithm, Digest Type, and Digest fields! Don't touch the keyData section as you won't get passed the validation. Only change the following four:
- Copy the Key Tag value
- Select no. 13: ECDSA/SHA-256 in the Algorithm field
- Select 2: SHA-256 in the Digest Type field
- Copy over the Digest
- Don't fill out the rest! :)
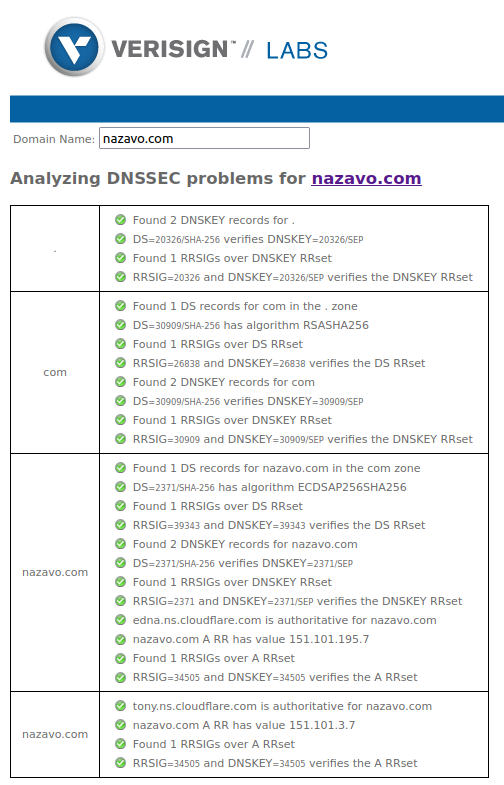
DNSSEC tools to validate configuration
Verisign Labs has a DNSSEC debugger allowing to check if the site has a correct DNSSEC configuration. Here is the output for nazavo.com domain after successful configuration:
If you are a command-line fan like myself, you can do a check for RRSIG and other DNSSEC related records on your domain using dig or delv. Below is an example running dig with +dnssec parameter for a correctly configured domain (man page reference):
➜ ~ dig +dnssec nazavo.com dnskey
; <<>> DiG 9.16.1-Ubuntu <<>> +dnssec nazavo.com dnskey
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 40986
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 1232
;; QUESTION SECTION:
;nazavo.com. IN DNSKEY
;; ANSWER SECTION:
nazavo.com. 3264 IN DNSKEY 257 3 13 mdsswUyr3DPW132mOi8V9xESWE8jTo0dxCjjnopKl+GqJxpVXckHAeF+ KkxLbxILfDLUT0rAK9iUzy1L53eKGQ==
nazavo.com. 3264 IN DNSKEY 256 3 13 oJMRESz5E4gYzS/q6XDrvU1qMPYIjCWzJaOau8XNEZeqCYKD5ar0IRd8 KqXXFJkqmVfRvMGPmM1x8fGAa2XhSA==
nazavo.com. 3264 IN RRSIG DNSKEY 13 2 3600 20210920060520 20210722060520 2371 nazavo.com. dFycsov3FYndjGl8/W8J4ncvmWFWBtthtnAf0danR4D/W0V7qqbr9WHN ciaB8fUabnE5X/mjWFeayLCITTOvjw==And here's an alternative using delv (online man page for reference). Note, there's no need for additional parameters. delv queries for DNSKEY and DS records to establish a chain of trust for DNSSEC validation by default:
➜ ~ delv nazavo.com
; fully validated
nazavo.com. 2 IN A 151.101.3.7
nazavo.com. 2 IN A 151.101.67.7
nazavo.com. 2 IN A 151.101.131.7
nazavo.com. 2 IN A 151.101.195.7
nazavo.com. 2 IN RRSIG A 13 2 2 20210823091622 20210821071622 34505 nazavo.com. 26WBPe0nxNfHqtF8eYyH6UYQdBDfwx6fX3CBIJBaeahSqVEfEGRBwXSv 89Pgl83GyMn6I7RMx2d3jcbsXCAwng==Fin
Check the domains you own now. Protect yourself from authoritative name server spoofing that may lead to losing control over your domain.
Security is easy to ignore, until it's not!
